Introduction
- In the face of conflict/annexation threats with WEF, CCP, USA, CANZUK, UK, EU, Transnational Cartels and Organized Crime Groups (OCG’s ~5000 groups), below is a comprehensive, technically robust set of recommendations designed to guide responsible citizens (PAL/RPALs) towards upgrading their security sophistication.
- Our aim is to guide the modern “Responsible Citizen Defender” in strengthening operational security (OPSEC), digital privacy, and resilience in the face of both everyday cyberthreats and more extreme international scenarios.
- Where relevant, we highlight potential pitfalls or oversights in the original security concepts and integrate broader best practices drawn from software engineering, cybersecurity, and privacy disciplines and combine with our own applied and in the field tech experiences learned from real world project engagement for Directors of Large Cap, Tier-1, American Tech Corporations.
1. General Philosophy of Security & Resilience
1.1 Layered Defense
- Security should never rely on a single product or trick.
- Use multiple overlapping defenses – e.g., a secure operating system (Ex: Qubes, Graphene OS, or older mainstream OS), robust network segmentation, strong encryption, physical security, good user behaviour, and strong backups.
1.2 Minimize Digital Footprint
- The less data you generate or store online, the harder it is for adversaries (whether criminals, hostile nations, or intrusive companies) to gather information on you or mount targeted attacks.
1.3 OPSEC & Risk Assessment
- Continuously assess how an attacker might target you. Use threat modelling: “What assets do I need to protect? Who might want them? What capabilities do they have?” Then apply solutions proportionate to those threats.
1.4 Legal & Ethical Compliance
- Familiarize yourself with local and national laws. Some recommendations (e.g., SDR listening or certain radio transmissions, purchasing encryption products, certain modifications to vehicles) can intersect with regulatory frameworks. Always verify legality before proceeding.
2. Operating Systems & Personal Computers
2.1 Linux Distributions
- Zorin OS can be user-friendly and more familiar to those coming from Windows or macOS, but also consider: Ubuntu LTS, Linux Mint, or Fedora for mainstream desktop usage.
- Qubes OS for high-security compartmentalization (more advanced users). Tails OS (live USB) for anonymity-critical tasks (though not for daily normal usage).
Rationale:
- Qubes OS uses virtualization to compartmentalize tasks – particularly useful for those who want the highest possible security posture.
- Tails OS is ephemeral (lives in RAM, leaves minimal traces), ideal for whistle-blowers or high-risk activism.
2.2 Windows Usage
- Avoid Windows XP for production or daily usage. XP no longer receives security patches and is extremely vulnerable. If absolutely needed to run legacy radio or hardware software, isolate it from the internet (air-gapped) and patch with unofficial or community updates as far as possible.
- Windows 10 or 11 (with all current patches) is safer but not as privacy-friendly out of the box. Consider manual tweaks (e.g., disabling telemetry), or using third-party firewall software to strictly control outbound connections.
2.3 macOS
- Older macOS versions (like Monterey or earlier) may be used instead of newer versions, but note that older versions eventually fall behind on security updates, and while the older versions might protect from Apple it might allow an opening from a third party attacker.
- Pertaining to laptops with built in AI chips, avoid this, such as Apple’s newer hardware with integrated AI/ML chips (M1/M2), you can remain on Intel-based Macs, but do keep the older Monterrey OS patched for security reasons, as much as is available for that OS level.
2.4 Hardware Considerations
- Lenovo Laptops are often recommended for Linux compatibility (e.g., ThinkPad lines). Just ensure you: Check the BIOS or firmware settings for possible remote management engines (e.g., Intel ME).
- Keep BIOS/UEFI updated and disable Intel AMT (Active Management Technology) if not needed.
- Avoid or minimize “hardware AI/Neural” co-processors on your daily driver if you suspect they leak data, but be aware many modern CPUs and SoCs have integrated AI-like functionality. Complete avoidance might not always be possible due to impracticality.
2.5 Data Minimization & Network Control
- Monitor System Traffic: Tools like Little Snitch (macOS) or OpenSnitch (Linux) provide fine-grained control over outbound connections, letting you see if idle machines are sending suspicious data.
3. Networking & Wireless
3.1 Ethernet Over Wi-Fi
- Use Wired Connections: Reduces wireless attack surfaces and passive surveillance. Especially important in critical or “stealth” usage scenarios.
- Shielded Twisted Pair (STP) or Cat6/Cat7 cables for improved noise immunity and potential EMI protection in high-EMF environments.
3.2 Wi-Fi Minimization or Hardening
- If Wi-Fi is needed: Use modern security standards (WPA3).
- Hide SSIDs only if that suits your threat model, but note hidden SSIDs don’t truly prevent detection by advanced scanners. Place your Wi-Fi AP centrally in your home and use directional antennas, if possible, to minimize outside signal leakage.
3.3 VPN & Tor Usage
- VPN: For obfuscating your IP, especially on public networks. Ensure your VPN provider is reputable, with strong no-logs policies. ProtonMail for Software VPNs.
- Look for a hardware router with a built in Open Source Unix style hardware VPN that is powered by powerful parallelized processor.
- Great hardware VPNs offer a seamless experience that will actually end up being used, unlike software VPNs, which end up often being shut down by frustrated users with slower connections or due to simply forgetting to turn it on when using the network.
- Tor: For anonymity-critical tasks. However, be aware it can draw surveillance attention from advanced adversaries.
4. Mobile Devices
4.1 Operating System & Hardware
- Avoid Smartphones with AI chips (e.g., the latest iPhones or Android flagships), but be aware that modern hardware always has sophisticated sensor arrays.
- Use older models from Samsung or LG that can still receive custom ROMs (LineageOS, GrapheneOS) or at least official security updates.
- GrapheneOS (Pixel hardware) or CalyxOS for privacy is recommended if you can accept some Google hardware.
- If you must remain truly account-less and minimal, keep the phone offline or in a Faraday pouch at home and during transport, except when needed.
4.2 Communication Apps & Practices
- Signal is still among the best widely available end-to-end encryption (E2EE) messengers.
- Session, Element (Matrix), Briar, Threema, or Wire are alternatives. Evaluate reliability, user base, and threat model.
-
Meshtastic with LoRa or Status (Web3) can provide fallback options in partial or full internet outages, but these are niche and require setup or specialized hardware. Lilygo online is easy to access the LoRa devices T-Beam and T-Deck.
-
Buy the latest variants that are built and work more seamlessly fully from provider like Rokland or LilyGo, as some of these devices are usually in beta, and can have bugs that can frustrate. Don’t take chances. Order complete systems.
4.3 Physical Mic & Camera Protections
- Tape over cameras or use a sliding webcam cover.
- Physical microphone disconnect or well-fitted microphone blockers can help.
- Keep your phone powered off or in a Faraday bag if worried about advanced location tracking or signals intelligence.
5. Software-Defined Radio (SDR) & Communications
5.1 SDR Usage
RTL-SDR v4


- For advanced usage, consider: Airspy or SDRplay for better dynamic range and sensitivity.

- SDR# (Windows-based) or Gqrx / CubicSDR on Linux are popular front-end GUIs.
- SDR++ is a cross-platform and open source SDR software with the aim of being bloat free and simple to use.
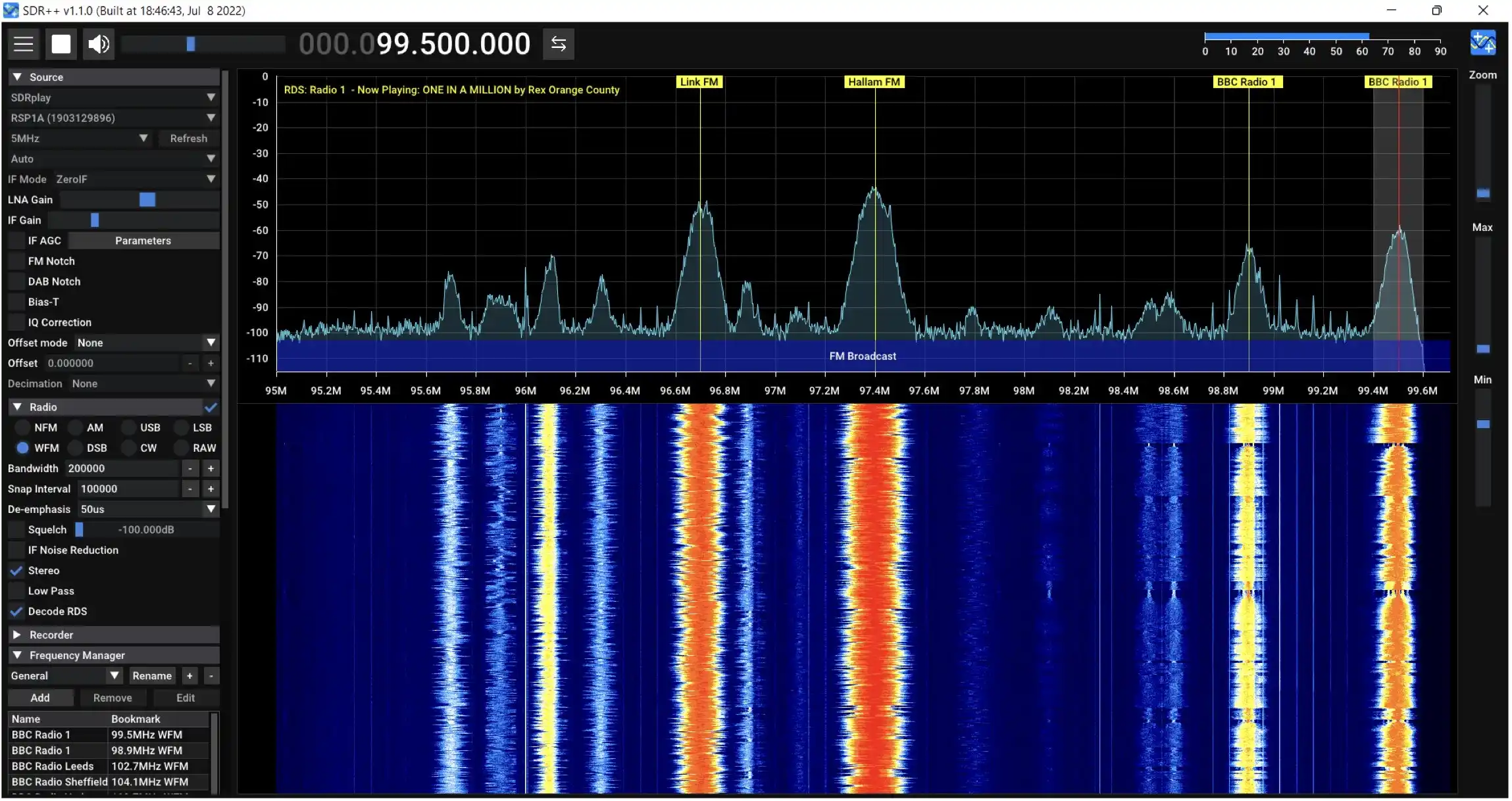
- Watch for local laws on scanning frequencies, especially those used by emergency services or private systems.

5.2 Radio Hardware & Backup Comms
- Baofeng 6X2 Pro DMR HAM or Anytone D878UV2 DMR HAM handhelds are high performance, and without spurious emissions, but check licensing requirements, legal frequencies, and encryption laws.
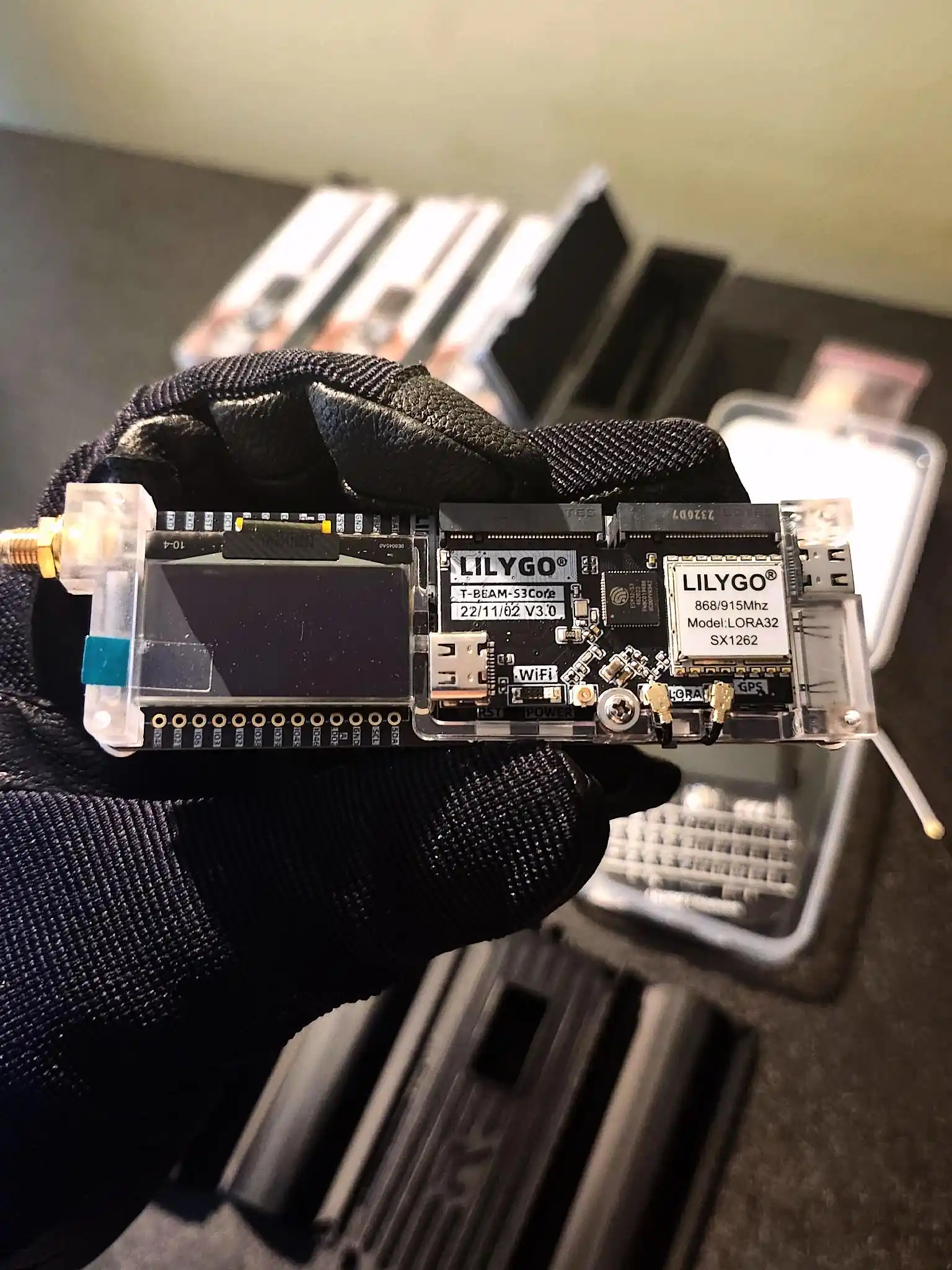
- For LoRa data networks: consider devices like LilyGO T-Beam SUPREME ESP32-S3 LoRa Development Board with SX1262 868/915MHz GPS U-Blox WiFi Bluetooth 1.3inch OLED






- And don’t forget to keep multiple copies of Meshtastic app installed across a few older Samsung or LG phones to pair with these devices.
- Keep in mind: “Encryption” on ham bands is often restricted. In an emergency or disaster scenario, these radios can be a lifeline but prepare responsibly and legally.
- There is also the option of licensing a business band or corporate band, for specialty use in a corporate business setting between members of an organization, and encryption can be used here, which is offered by the two previously mentioned radios.
5.3 Enhancing Communication Range with a Mobile VHF/UHF Amplifier
- In a crisis scenario, maintaining reliable long-distance communication is crucial. Handheld radios like the BTECH DMR-6X2 PRO are excellent for portability but have limited power output. To extend their effective range and improve signal clarity, a VHF/UHF amplifier can be a game-changer, especially for mobile and vehicle-based operations.

Why You Need It for Operational Security (OPSEC) & Crisis Readiness
- Extended Range for Tactical Coordination – In emergencies, riots, or rural operations, standard 5-7W handheld radios may struggle to reach across long distances or penetrate dense environments (buildings, forests). Boosting output to 40W ensures stronger signal penetration and reliable long-range communication.
- Vehicle-Based Mobile Communications – Integrating this amplifier into a Toyota Tacoma, Ford F-150, or any off-road-ready vehicle converts the mobile station into a powerful communication hub, ideal for maintaining contact with a decentralized security network or backup teams.
- Emergency & Disaster Response – If internet, cell networks, or conventional infrastructure collapse, maintaining encrypted or analog communications over long distances via VHF/UHF radio waves ensures operational effectiveness. The AMP-V25D allows team coordination over dozens of miles in extreme scenarios.
-
Covert Operations & Signal Security – Using the amplifier in conjunction with directional antennas, encryption-capable DMR radios (6X2 PRO, Anytone D878UV2), and LoRa-based mesh relays can significantly increase the resilience of the comms network against surveillance, jamming, and digital tracking attempts.
How to Integrate the AMP-V25D with the BTECH 6X2 PRO
- Power Setup: Use a 13.6V battery system (compatible with your EMP-hardened vehicle power grid or a solar-charged power pack). Ensure your system can handle 6A peak draw.
- Connect Your Handheld Radio: The included Kenwood-style 2-pin PTT cable ensures seamless connectivity between the DMR-6X2 PRO and the amplifier.
- Antenna Considerations: For maximum range, use a NMO-mount mobile antenna (VHF/UHF dual-band) with a 5dBi gain or higher.
-
Avoid low-quality magnetic-mount antennas, as they may cause RF losses. In a fixed base-station setup, a high-gain Yagi or vertical omni-directional antenna further extends communication range.
-
Mode Optimization: When using digital modes (DMR Tier II, P25, or System Fusion), ensure low-latency repeater access to avoid signal dropouts.
Legal Considerations & Compliance
- Ensure that output power levels and frequency allocations comply with local regulatory frameworks (FCC, ISED, OFCOM, etc.)
- Licensed ham operators or emergency coordinators should consider business or public safety bands if encryption is required.
- Avoid interference with first responders, military frequencies, or aviation bands unless operating under legal authorization.

Final Thoughts
- Adding the BTECH AMP-V25D to the responsible citizen defender setup dramatically improves tactical communication range, making it an essential tool for emergency preparedness, covert operations, and long-range off-grid networking. Whether used in a vehicle, bug-out convoy, or fixed base station, this amplifier ensures stronger, more resilient, and more secure radio communications in both urban and off-grid scenarios.
6. Energy Resilience & EMP Protection
6.1 Battery Packs & Generators
- Bluetti AC180 or similar LiFePO4-based packs are good. For even more robust or modular setups, compare models from Goal Zero, EcoFlow, or Jackery.

- Solar Panels: High-watt foldable or portable panels (briefcase kit) can keep your station off-grid. Factor in inefficiencies, daily sunshine, and safe storage.
6.2 Vehicle EMP Hardening
- Install “DEFCON” EMPvehicle surge protection switch on the Ford F-150 or the Toyota Tacoma trucks, two high saturation ferrite chokes on sensitive lines from battery and TRAPs for the computer ODB port, for the vehicle plug, and for the battery.
- Be cautious with the traps, but it does offer decentralize net of anti EMP surge control mitigation.
- Physical Faraday storage for smaller devices (e.g., laptops, radios, external HDDs) can ensure critical electronics survive potential EMP events.
- Always confirm performance with proven testing or recognized community references.
7. Data Security & Backup
7.1 Encryption & Storage
- Use Full Disk Encryption on all laptops/devices (e.g., LUKS on Linux, FileVault on macOS, BitLocker on Windows).
- Password Managers (KeePassXC, Bitwarden) to handle strong unique passwords.
- For highly sensitive data, use an air-gapped offline password vault or physically write them (secured in locked safe).
7.2 Backup Strategy
- 3-2-1 Rule: 3 copies, on 2 different media types, 1 off-site or offline.
- Keep at least one cold offline backup (no internet access) to protect against ransomware or advanced intrusions.
7.3 Network & App Controls
- Tools like Little Snitch (macOS), OpenSnitch (Linux), or GlassWire (Windows) give real-time outbound connection oversight.
- Consider Pi-hole or AdGuard Home at the router level to block trackers and malicious domains system-wide.
8. Personal AI and Compute Power
8.1 Running Local Large Language Models
- NVIDIA or AMD GPU can host open-source LLMs (e.g., LLaMA derivatives) for local inference.
- Secure the environment with containerization or VMs.
-
Beware bandwidth usage if the model tries to phone home. Monitor traffic or keep it fully offline.
8.2 Privacy & Intellectual Property
- Locally hosted AI keeps your data away from third-party servers, but watch out for any downloaded model weights that might contain hidden code or vulnerabilities. Verify checksums from reputable sources.
9. Additional Security Tooling & Hardening
- Host-Based Firewalls & IDSOSSEC, Wazuh, or Zeek can provide intrusion detection or log analysis on a home network.
- Sandboxing & Virtualization: For unknown or risky software, run in a disposable VM or container. Tools like Firejail (Linux) can isolate apps.
-
Secure Boot & BIOS Protections: Enable UEFI Secure Boot (with caution if using Linux) to prevent bootkits. Set BIOS/UEFI passwords.
-
Physical Anti-Tamper Measures: Use tamper-evident tape on laptop chassis or external ports to detect covert hardware implants. Store devices in locked containers and EMP boxes when not in use.
10. Maintaining Operational Security (OPSEC)
- Situational Awareness: Keep track of who might be monitoring you (neighbours, local criminals, advanced adversaries, corporations, telecom agent from public safety divisions, social media monitoring). Adjust your posture accordingly.
- Separate Personas: For highly sensitive tasks, use separate devices or Qubes OS compartments. Don’t mix “casual browsing” with “sensitive operations” on the same user account or device.
- Email Hygiene: Use encrypted email (ProtonMail, Tutanota) or GPG with standard providers for sensitive communications. Avoid linking personal accounts to “anonymous” communications.
-
Browser Hardening: Use privacy-focused browsers (Firefox hardened, Brave) with add-ons like uBlock Origin, HTTPS Everywhere, Privacy Badger. Manage scripts via NoScript if advanced threat model.
11. Continuous Learning & Community
- Stay Informed: Security is not “set and forget.” Follow reputable cybersecurity blogs, mailing lists, podcasts, or local ham radio clubs to remain aware of new vulnerabilities or best practices.
- Practice Drills & Training: Regularly test your backups, radio equipment, and power solutions. Doing so reveals weaknesses in your planning.
- Contribute & Collaborate: Join local prepper, amateur radio, or cyber-security communities to share knowledge, ask questions, and refine skill sets. Embrace open-source communities that actively audit and improve the tools you rely on.
12. Key Caveats & Final Thoughts
- Balance vs. Usability: The more security you implement, the more cumbersome day-to-day usage can become. Tailor your setup to your actual threat model; over-complicating can lead to mistakes or fatigue.
- Legal & Ethical: Some gear (powerful SDRs, certain encryption or radio frequencies, firearms, vehicle modifications, etc.) may require licenses or be restricted in your jurisdiction. Ensure compliance to avoid unintended legal issues.
- Evolving Landscape: Threats (and solutions) evolve quickly. Resist the urge to rely on a single “static” plan from 2025 if circumstances significantly change by 2030. Periodically reassess.
-
Health & Mindset: True resilience includes mental well-being. Overwhelming paranoia can degrade your quality of life. Find a balanced approach that allows you to remain vigilant yet still functional and happy.
Conclusion
- By strengthening these areas — choosing the right OS, securing mobile devices, controlling radio signals, ensuring power resilience, encrypting data, and adopting disciplined OPSEC — the “Responsible Citizen Defender” can significantly reduce exposure to modern surveillance and cybersecurity threats.
- Ultimately, the best defense is thoughtful, continuous improvement in habits and technology usage. No single product or step guarantees perfect security, but a layered, well-informed approach can drastically raise the bar for any adversary, while preserving your privacy and digital autonomy in an increasingly complex and interconnected world.


Appendix – Mission Files:
- A dim blue glow illuminated the ThinkPad’s keyboard as SGT Valentin ran a final scan on the network. The custom-built firewall dashboard showed an anomaly — an unauthorized ping attempting to access a secure LoRa relay.
- A breach attempt.
-
With swift keystrokes, Valentin traced the signal’s origin. An AI-powered surveillance drone had just registered movement in the target zone. The encrypted Meshtastic uplink was still secure, but the perimeter was compromised. The mission window had just shrunk.
Phase 1: The Digital Counterstrike
- Valentin activated a custom SDR jammer, feeding false telemetry data back to the enemy drone. On their end, it would appear as if a ghost signal had replaced the real-world coordinates. The drone would chase shadows, buying time.
- He sent a LoRa-secured message to the rest of the SGT Operative Team:
“Network breach detected. Digital misdirection in progress. Move now.”
- Across the city, a Sovereign Guardians of Tranquility (SGT) recon team moved out, their communication running through a private, AI-hardened VPN deployed on open-source routers.
- Time was against them.
Phase 2: Physical Extraction
- Outside, his Toyota Tacoma — EMP-hardened and loaded with encrypted communications gear— waited.
- The city was alive with silent watchers — rogue drones, cartel informants, government AI spiders tracking digital footprints.
-
The SGT team had one chance to extract the target: a whistleblower engineer carrying proof of classified surveillance abuses by a powerful transnational entity working with the Prime Minister against Canada.
“If this data gets out,” Valentin thought, “it could shift the balance of digital power forever.”
- The mission demanded complete operational security. The exfiltration plan? A decentralized, encrypted off-grid relay.
Phase 3: The Pursuit
- As Valentin navigated through the city’s underpasses, an alert popped on his LoRa receiver — a surveillance car was tailing them.
- He tapped into a high-gain antenna, connecting to the SGT team’s private SDR frequency. A voice crackled through.
“Multiple pings on your position. Five minutes before interception. Adjust route.”
- Valentin flipped a hidden switch on the dash, activating a mesh-networked counter-surveillance algorithm. His vehicle’s AI defense system scrambled its digital footprint, feeding false GPS locations to hostile trackers.
- The tailing vehicle hesitated — chasing phantom signals.
Phase 4: The Unexpected Enemy
- Just as he reached an underpass near the extraction zone, the LoRa receiver blared another alert — this one different.
- A high-frequency encrypted signal was broadcasting across multiple channels. Someone was tracking them, but this wasn’t a normal surveillance drone or cartel informant.
-
A figure stepped into the street — a woman clad in a sleek, high-tech bodysuit, her eyes glowing with cybernetic augmentation. She moved with an unnatural precision, her neural interface jacks pulsing faint blue. A transhuman agent.
“SGT Valentin, you have something that doesn’t belong to you. Hand over the drive.”
- Her voice was cold, synthetic. The drones circling overhead had recalibrated, locking onto his position. This wasn’t just a breach — it was a full-scale digital war.
- Valentin didn’t hesitate. He activated his wrist-mounted tactical HUD and ran a rapid scan. Her bio-signature was augmented— enhanced reflexes, combat prediction algorithms, and a tactical AI feeding her data in real-time.
“You should walk away,” Valentin said, gripping his plasma blade.
- She smirked. “Let’s test that theory.”
Phase 5: Cybernetic Combat
- She moved first, faster than any human should. Valentin barely deflected her energy katana in time, sparks flying as metal clashed against plasma. The AI drones repositioned, feeding her telemetry as she adjusted her attack.
- Valentin activated a micro-EMP burst, disrupting the drones for a fraction of a second — enough time to counter. He struck back, using his LoRa networked wrist device to predict her movements. The battle became a dance of light and data, a fight between a man and the cutting edge of transhuman warfare.
- But he wasn’t alone.
- Asudden explosion from above disrupted the fight. The SGT team had arrived, firing EMP-hardened rounds that scrambled nearby surveillance drones. The transhuman cyborg hesitated — just long enough for Valentin to disengage and sprint toward the extraction point.
- The Toyota Tacoma’s AI-assisted defenses engaged, automatically jamming incoming enemy signals. Valentin threw himself into the driver’s seat and slammed the accelerator.
“Fall back to secure relay point,” he ordered. “We’ve got bigger problems than just a data breach.”
Phase 6: The Final Firewall
- They reached the secure extraction point — a rural station deep within a shielded LoRa mesh network.
- The whistle-blower, visibly shaken but determined, handed over the drive. Valentin inserted it into an air-gapped laptop, checking for malware payloads or tracking beacons. Clean.
-
The data was encrypted and routed through a secure, AI-assisted quantum-safe relay— uploading across a decentralized, censorship-resistant network.
-
But the battle wasn’t over. The trans-human agent had regrouped, and a swarm of reinforcements was inbound.
“We need an exit. Now.”
- Valentin activated the final failsafe. The EMP grid detonated, sending a wave of disruption through the area. Drones flickered and spiralled down, their circuitry fried.
- The trans-human agent stood at the edge of the blast radius, watching them retreat into the darkness.
“We’ll meet again, SGT Valentin,” she said, her voice carried through an encrypted channel. “You can’t stop what’s coming.”
- As dawn broke, Valentin and the SGT team disappeared into the network, their traces erased.
- The battle for digital and physical freedom had just begun.
- The world may not know their names.
-
But the Firewall remains standing.


Related Content:
Title: “Powering the Future: The Heroic Journey of Transcendent STEM Professionals in Age of Convergence” https://skillsgaptrainer.com/powering-the-future/
Title: “Transcending Limits: Embracing Nietzsche’s Übermensch in the Age of AI and Powered Assault Armour”https://skillsgaptrainer.com/transcending-limits-embracing-nietzsche/
Title: “Transcending Limits: Embracing Nietzsche’s Übermensch in the Age of AI and Genetic Enhancement” https://skillsgaptrainer.com/transcending-limits/
Title: “SGT Tech Showdown: BTECH DMR‑6X2 PRO vs. Anytone AT‑D878UVII Plus”https://skillsgaptrainer.com/sgt-tech-showdown-btech-dmr%e2%80%916×2-pro-vs-anytone-at%e2%80%91d878uvii-plus/
Title: “Meshtastic Unveiled: Revolutionizing Decentralized Communication for a Resilient Future” https://skillsgaptrainer.com/meshtastic-unveiled/
Title: “LILYGO® Meshtastic T-Beam SUPREME ESP32-S3: A Comprehensive Guide to Next-Generation Off-Grid Communication” https://skillsgaptrainer.com/lilygo-meshtastic-t-beam-supreme-esp32-s3/
Title: “LILYGO® Meshtastic T-Deck ESP32-S3 LoRaWAN: A Comprehensive Guide to Long-Range Communication” https://skillsgaptrainer.com/lilygo-meshtastic-t-deck-esp32-s3-lorawan/
Title:“BTECH DMR-6X2 PRO: A Comprehensive Guide to Next-Generation Radio Communication” https://skillsgaptrainer.com/btech-dmr-6×2-pro-a-comprehensive-guide/
Title: “Preserving the 900 MHz Band: Empowering Communities with LoRa for Resilience & Security”https://skillsgaptrainer.com/preserving-the-900-mhz-band/
THE CCFR – Canadian Coalition of Firearm Rightshttps://firearmrights.ca/
Skills Gap Trainer https://skillsgaptrainer.com
Ham Radio Crash Course https://www.youtube.com/@HamRadioCrashCourse
T.REX ARMS https://www.trex-arms.com/
T.REX ARMS (YouTube Channel) https://www.youtube.com/@TREXARMS
T.REX LABS https://youtu.be/nNEHPiEcCMY?feature=shared
Tactical Hyvehttps://www.youtube.com/@TacticalHyve
Dirty Civilian https://www.youtube.com/@dirty-civilian
MDT SPORTING GOODS LTD https://mdttac.ca/
BlackCreek https://www.blackcreeklabs.com
Lockhart Tactical https://www.lockharttactical.com/
I.P.S.C. BC https://ipscbc.com/
Canadian Shooting Sports Associationhttps://cssa-cila.org/
Canadian Sniper Association https://canadiansniperassociation.com/
National Firearm Association https://nfa.ca/
Fix the broken countries of the west through increased transparency, design and professional skills. Support Skills Gap Trainer.’
To see our Donate Page, click https://skillsgaptrainer.com/donate
To see our YouTube Channel, click https://www.youtube.com/@skillsgaptrainer



